Drones are hot. They come in all sizes and price ranges and are used for private and surveillance purposes. By individuals, companies, governments but (unfortunately) also by criminals and terrorists.
Since time immemorial, towers and lookout posts on hills and mountains have been used to gain optimal visibility over the (defense) area. Later came zeppelins and hot air balloons. At the beginning of the last century, aircraft were deployed for the first time during wars. Initially for reconnaissance, later also for combat. By the end of World War I, the role of military aircraft had changed from that of ‘assistant’ to ground forces to that of an important independent fighting force. Warfare in 2D became a 3D battlefield with the advent of aircraft.
And now there is the drone. This too is deployed for military purposes; for reconnaissance and for attacks (particularly to eliminate very targeted targets). Drones can also be deployed to secure civilian objects. For example, to assess the situation after an alarm by capturing images of the area around the alarm position. Or by conducting surveillance. The advantages of this modern aerial reconnaissance are clear: quick to deploy, fast on location, able to search a large area in a short time, and not immediately noticeable from the ground. Moreover, from the air you have the ability to look behind objects.
Incidentally, it is not so much the images from this aerial reconnaissance that are interesting, but especially the information that can be extracted from linking these images with information from other sources, such as fire detection, alarm verification, and emergency calls. By linking information from carefully selected sources, a so-called Common Operational Picture (COP) can emerge. This gives the control room a clear picture of the situation on site and allows a situation (for example, an incident) to be handled efficiently with the most suitable, available resources.
Drone deployment
A drone can be deployed manually in response to an alarm. As soon as an alarm comes in, it is assessed whether it makes sense to deploy a drone to investigate the situation. If so, an available (certified) ground pilot is called up. This pilot is then instructed regarding the alarm location and the control room can monitor the pilot’s screen to assess the situation on site. It goes without saying that this approach wastes valuable time.
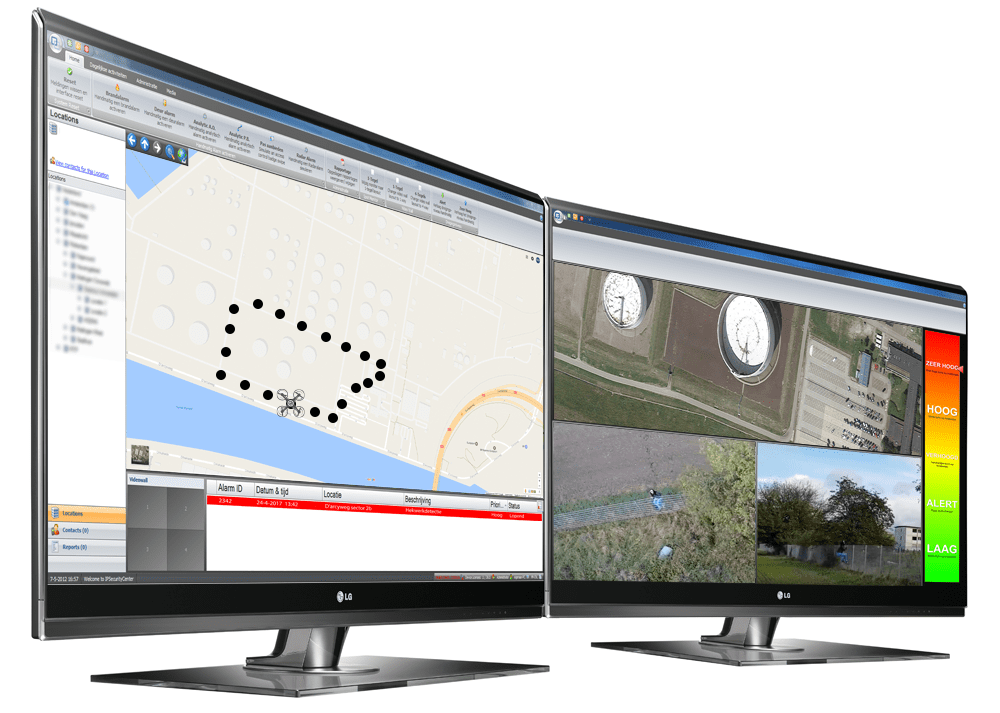
PSIM waypoints drone
Much more efficient is when the drone is integrated into the security systems of a location. A PSIM (Physical Security Information Management) system can automatically execute certain predefined follow-up actions based on a situation (alarms or observations). For example, dispatching one or more drones for a reconnaissance flight. Some PSIMs, such as IPSecurity Center, are already configured for drone deployment and translate the X/Y coordinates of the alarm location into a flight plan for the drone(s). Once the drone is in the target area, it provides the (thermal) camera images and certain (meta)data via the Video Management System for processing by the PSIM. During the action, the operator gets a good picture of the situation on site using the images and data. Depending on the situation and the capabilities of the drone, an intruder can subsequently be tracked automatically.
An important advantage of this automated approach is, in addition to the time savings, the fact that the flight plan is tailored to the location and thus dangerous flight situations are prevented. Moreover, all actions, the entire flight, the images, and the sensor information are recorded in the PSIM. This is important for evaluation purposes and to demonstrate with audit trails that proper action was taken.
3D protection
The advent of the drone thus offers many new opportunities, but also threats. Drones can be deployed for reconnaissance, attack, and defense. As part of a security system, as a tool to create situational awareness, and as a weapon. Drones are not hindered by fencing or inaccessible floors, they fly over security guards and remain out of sight of security cameras, which are usually not aimed at the sky. Drones pose a threat from the air and if we want to adequately protect ourselves against this, we will need to adopt a 3D security approach.
Currently, the use of drones is subject to safety and privacy regulations, which limits their deployment as a security measure. Due to increasing threats, it is expected that this will change in the near future, allowing drones to be deployed more frequently and effectively. Internationally, there are already various situations where exemptions have been granted to deploy drones.
