We often write about how to identify and delay criminals. But how great would it be if we could discourage them altogether? So they don’t even attempt an attack. At least not on your organization…
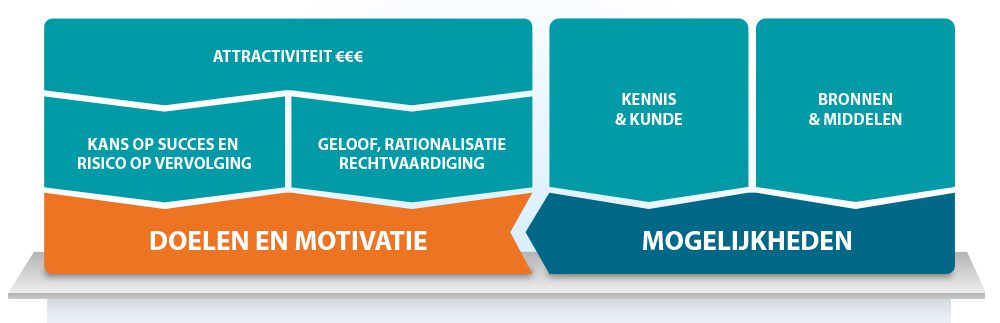
To know how to discourage criminals, we first need to understand how criminals and their organizations operate, because we’re dealing with organized crime here. Criminals strike only when there is an attractive and accessible target. Furthermore, the likelihood of getting away with the loot and being able to use it (motivation) must be high. Other prerequisites include having enough knowledge or being able to gather it about the target organization and possessing the right tools (such as equipment, getaway cars, etc.) and skills (capabilities).
Meticulous preparation
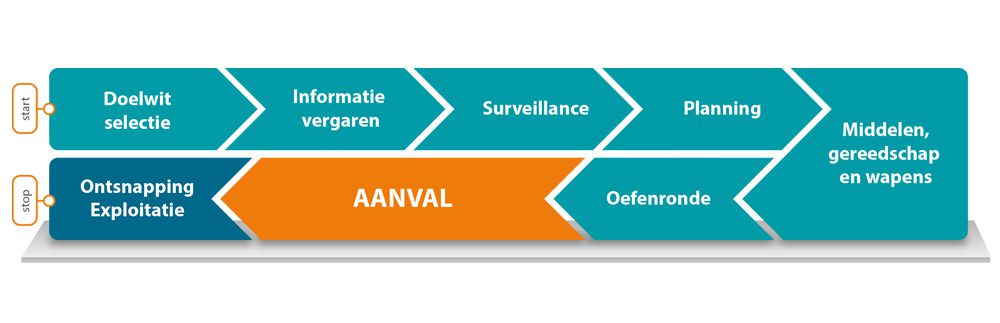
Professional criminals carefully prepare their attack. They prefer to take as few risks as possible and therefore work in a very systematic manner. After selecting a potential target, they begin with a “criminal SWOT analysis.” They list the opportunities and threats and assess the strengths and weaknesses. To do this, they gather information in every possible way, for instance, by observing their target and collecting intelligence via social media or personal contacts. Based on the knowledge gathered, they make a go/no-go decision. They decide whether an attack is worthwhile or if they should move on to another target.
After the decision to attack is made, the criminal organization plans the attack thoroughly, and the necessary tools are gathered. Sometimes the organization even conducts a so-called “dry run” before executing the actual attack to verify that the planned attack scenario works in practice.
Deter and prevent an attack in 3 steps
If your organization is a potential target, it is crucial to undermine this criminal business case as quickly as possible. The closer to the actual attack moment, the harder it becomes to get the criminals to abandon their plan. Prevent an attack by following these three key steps:
1. Secrecy (DENY)
Ensure that criminals cannot access critical information (online, on paper, or through employees) that they need for planning an attack. For example, information about who works at your organization, the routines, and the security measures in place. If they cannot find or access this information, criminals become uncertain. They can no longer determine when and where to attack for a successful outcome. This uncertainty can make your organization less attractive than comparable targets where information is available.
2. Detection (DETECT)
Detect any attempts by unauthorized individuals to request or gather information. Camera systems can detect suspicious movements around your premises. Ensure that employees stay alert and that your suppliers do not leak information (stories, references, photos). Also, confirm that you are notified by the local municipality if someone requests building plans for your premises. The goal is to make it as likely as possible that criminals are caught while collecting information, in whatever way they try to do it.
3. Deterrence (DETER)
Deterrence is about communicating the likelihood of failure and uncertainty. Communicate that gathering information is impossible and that if someone attempts reconnaissance or information gathering, they will be detected immediately. Also, communicate that an actual attack will be spotted early on. Show that the physical security measures you’ve implemented are solid. Indicate that a strong and adequate response will cause the attack to fail, and that the likelihood of being caught in the act is high. Criminals will quickly realize if this is not the case. By doing this, you influence their perception. They will see your organization as a difficult target. Even though the potential loot is attractive, the risk of failure is high, and excessive effort would be required. For them, your organization becomes a bad business case. In most cases, they will therefore choose to abandon an attack on your organization and focus on a less secure target.
A ladder at the neighbors…
Finally, it’s important to be aware of your surroundings. What is happening with your neighbors, competitors, or similar organizations? The less attractive you are (compared to others) or the stronger your security, the more likely criminals will perceive you as too difficult a target. It’s important to periodically reassess this because the situation at your organization and others can change rapidly.
Be prepared if they come!
However, a solid deterrence strategy does not guarantee they won’t come. Not all criminals make a good business case, and some may find the potential loot at your organization irresistible. In addition to having an integrated security plan, physical security measures are also necessary. This will delay any potential attack, giving enough time for response (mobilizing and having the right responders on-site).
