Door de toename van bedreigingen en veiligheidsrisico’s zijn bedrijven en organisaties op zoek naar middelen om hun processen en locaties efficiënt en effectief te beveiligen. Een oplossing die in dat verband vaak voorbij komt, is een Physical Security Information Management (PSIM) systeem. Maar wat is nu precies een PSIM? En is dat ook wat u zoekt, of volstaat een Security Management Systeem (SMS)?
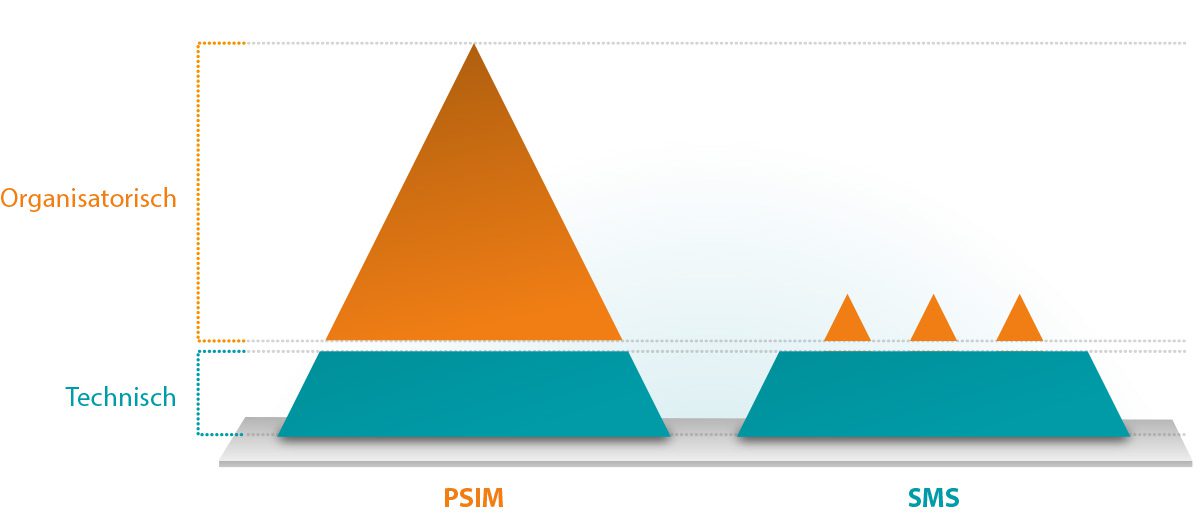
Door de groei van IP-gebaseerde beveiligingssystemen is er in de afgelopen 15 jaar een ontwikkeling geweest van losse, enkelvoudige systemen (zoals een toegangsbeheer-, camerabewakings-, inbraakmeld- en branddetectiesysteem) naar meer geïntegreerde oplossingen. Deze systemen werden bovendien steeds veelzijdiger en uitgebreider. Zo ontstonden Security Management Systemen, die veel van de aanwezige enkelvoudige systemen verenigen en ook PSIM oplossingen die nog een stap verder gaan en bedoeld zijn om (crisis) situaties te managen en snel onder controle te krijgen.
Security Management Systeem
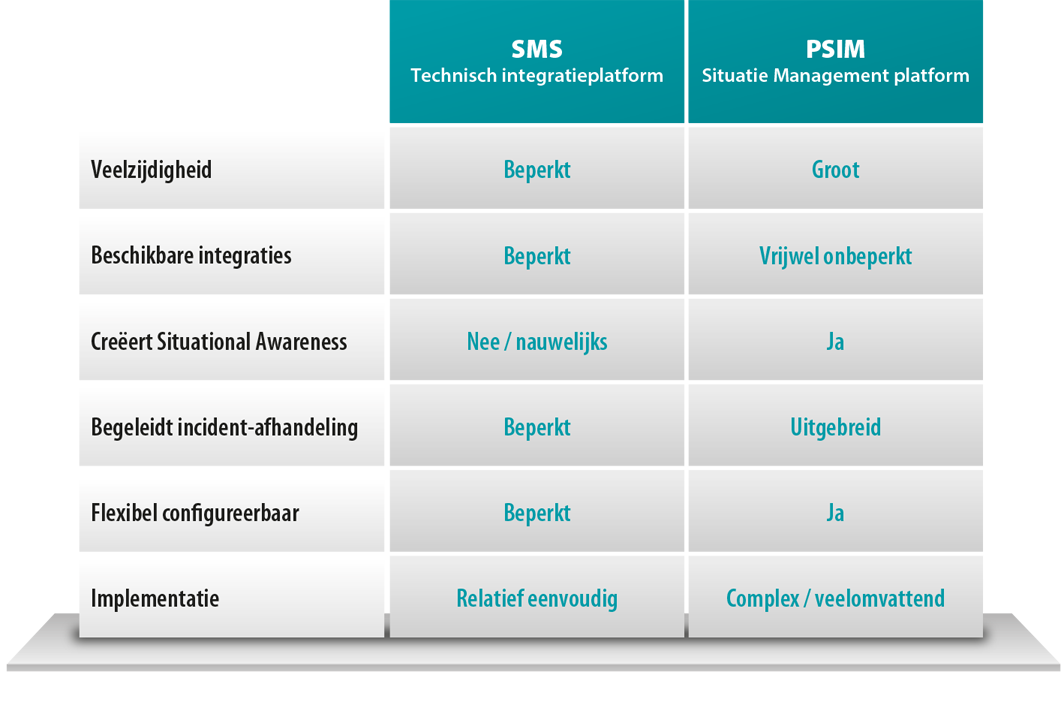
Met een SMS kunnen de individuele safety en security systemen aan elkaar worden gekoppeld en centraal worden bediend, vanuit één applicatie. Om de verschillende beveiligingssystemen te bedienen, is geen diep-gaande kennis van de onderliggende beveiligingssystemen meer noodzakelijk, maar enkel kennis van het SMS.
Een SMS verzorgt ook de interactie tussen verschillende beveiligingssystemen, bijvoorbeeld door een camerabeeld te koppelen aan een ‘event’ in het toegangsbeheer- of inbraakmeldsysteem. Bovendien kan een SMS een filterende werking hebben en alleen een alarm genereren bij events die aan bepaalde criteria voldoen. Zo beschikken gebruikers continu over de meest relevante informatie. Meestal is een SMS gebaseerd op een toegangsbeheersysteem of een Video Management Systeem (VMS), met extra functionaliteiten en integraties. De basisconfiguratie gebeurt nog steeds in de onderliggende systemen, die autonoom functioneren.
Physical Security Information Management
Door ernstige incidenten zoals 11 september 2001, de aanslagen in de metro van Londen en recente aanslagen in Parijs, Berlijn en Keulen is de behoefte aan PSIM systemen toegenomen. PSIM systemen zijn door softwarebedrijven ontwikkeld vanuit de visie dat het bij (ernstige) incidenten essentieel is om de situatie ter plaatse in al zijn aspecten goed ‘in beeld’ te hebben, inclusief het dreigingsniveau. Zodat operators het incident volledig overzien en altijd de juiste maatregelen nemen. Bij (ernstige) incidenten mag de interpretatie van gegevens en beelden immers niet volledig afhankelijk zijn van een operator en diens kennis of ervaring. De nadruk ligt bij een PSIM op het managen en snel onder controle krijgen van (crisis)situaties, waardoor schade kan worden voorkomen of beperkt.
Door de koppeling van een groot aantal externe (beveiligings-)systemen in een PSIM kunnen logische verbanden worden gelegd en worden operators in crisissituaties begeleid met een realtime Common Operational Picture en stapsgewijze responsplannen. Met de software toolbox kan een command & control infrastructuur worden opgezet, gericht op crisismanagement. Een PSIM is hard- en software onafhankelijk; via connectoren wordt data uit onderliggende systemen gehaald en in het PSIM toegankelijk gemaakt.
Wanneer een SMS?
Organisaties hebben vaak diverse systemen in gebruik voor de beveiliging van gebouw(en) of terrein. Deze functioneren soms afzonderlijk van elkaar en soms gekoppeld aan elkaar. Ieder systeem heeft een eigen interface met eigen wachtwoorden en eigen logica. Een nachtmerrie vanuit beheersoogpunt en ook vanuit security oogpunt is dit niet optimaal. Beveiligingsrisico’s worden pas optimaal beheerst wanneer de technische installaties samenwerken en er snel geschakeld kan worden. Bijvoorbeeld het opschakelen van camerabeelden bij een indringer of ter verificatie van een brand. Dit kan met een SMS.
Er zijn verschillende SMS systemen beschikbaar. Sommige systemen zijn open voor koppelingen met systemen van andere merken, andere SMS systemen zijn volledig gesloten. Dat is dus een aandachtspunt als u een SMS selecteert. Juist de mate van openheid bepaalt de toegevoegde waarde. Immers, hoe meer slimme koppelingen en logica ingebouwd kunnen worden, hoe beter uw systemen kunnen samenwerken en hoe beter de risico’s worden beheerst. In een SMS kan in veel gevallen een eenvoudig script worden opgeroepen om de opvolging van incidenten volgens een standaard flow te laten verlopen, inclusief een logfunctie. Toch zijn deze functies in een SMS beperkt, omdat de nadruk ligt op de integratie van technische systemen en niet op organisatorische processen en procedures.
Een SMS is vooral geschikt voor middelgrote organisaties met een beperkte complexiteit en verscheidenheid aan beveiligingssystemen. Door deze systemen te integreren met een SMS kunnen de systemen centraal worden bediend. Er ontstaat synergie, doordat de gekoppelde systemen meer intelligentie en dus een hoger beveiligingsniveau bieden dan de optelsom van de separate systemen. De investering in een SMS is beperkt en het rendement groot.
Wanneer een PSIM?
Organisaties met complexe processen en waarbij de gevolgen van een calamiteit verstrekkend kunnen zijn, zouden beter voor een PSIM kunnen kiezen. Een PSIM integreert safety en security systemen én procedures en functioneert daardoor als het hart van de safety en security in een organisatie. Met een PSIM worden operators en alle andere interne en externe betrokkenen optimaal ondersteund bij het afhandelen van (crisis)situaties. Zij krijgen direct alle relevante informatie (ook uit gekoppelde databases of systemen zoals productie-, proces-, HR- , IT- gebouwautomatiserings- of bezoekersregistratiesystemen) om gezamenlijk de situatie zo snel en goed mogelijk af te handelen. Een PSIM kan ook de risicoaansprakelijkheid beperken, onder andere doordat alle handelingen worden gelogd en er een volledige audit trail beschikbaar is.
Het succes en rendement van een PSIM wordt grotendeels bepaald door de inrichting en implementatie. Er moeten processen in kaart worden gebracht en afwijkingen worden gedefinieerd, net als realistische (be)dreigingen en scenario’s. De bijbehorende opvolgingsprocedures moeten (tot in detail) worden uitgewerkt om deze vervolgens in het systeem op te nemen in de vorm van (dynamische) workflows. Hoe beter dit gebeurt, hoe effectiever het PSIM voor de organisatie zal zijn. Meestal wordt voor een PSIM implementatie een team aangesteld met betrokkenen uit de gehele organisatie en zowel ICT als safety en security experts.
Er zijn verschillende PSIM systemen beschikbaar, die met name verschillen in de mate van flexibiliteit en gebruiksvriendelijkheid. Niet alleen moet u kiezen voor het voor uw organisatie meest geschikte PSIM systeem, ook de leverancierskeuze is in dit geval van groot belang. Voor een dergelijke complexe beveiligingsoplossing is ruime ervaring en deskundigheid vereist. En dat gaat verder dan technische kennis; met name het implementatie- en beheertraject waarbij opdrachtgever en leverancier nauw moeten samenwerken, zijn van grote invloed op het succes en rendement van de gekozen oplossing.
Conclusie
De keuze om losse systemen technisch te integreren door middel van een SMS verhoogt in veel gevallen het beveiligingsniveau. Dit vergroot het bedieningsgemak en haalt het maximale uit de onderliggende systemen. De implementatie is overzichtelijk en de kosten zijn beperkt. Een PSIM gaat een stap verder. Met een PSIM worden ook de organisatorische aspecten van beveiliging ondersteund en geoptimaliseerd. Er kan aanzienlijk worden bespaard op de beveiligingskosten en – nog belangrijker – bedreigende situaties zijn sneller onder controle. Door de vroegtijdige herkenning en adequate afhandeling kan schade worden beperkt of voorkomen. Voor beide oplossingen geldt, dat het succes ervan valt of staat bij de implementatie en de kennis en ervaring van de leverancier.

