Are your company locations secured with one integrated security (management) system? Then it is important to ensure that data exchange between locations is done securely. A VPN (Virtual Private Network) connection based on the Internet Protocol is an affordable and transparent way to achieve this. In this article, we explain how it works.
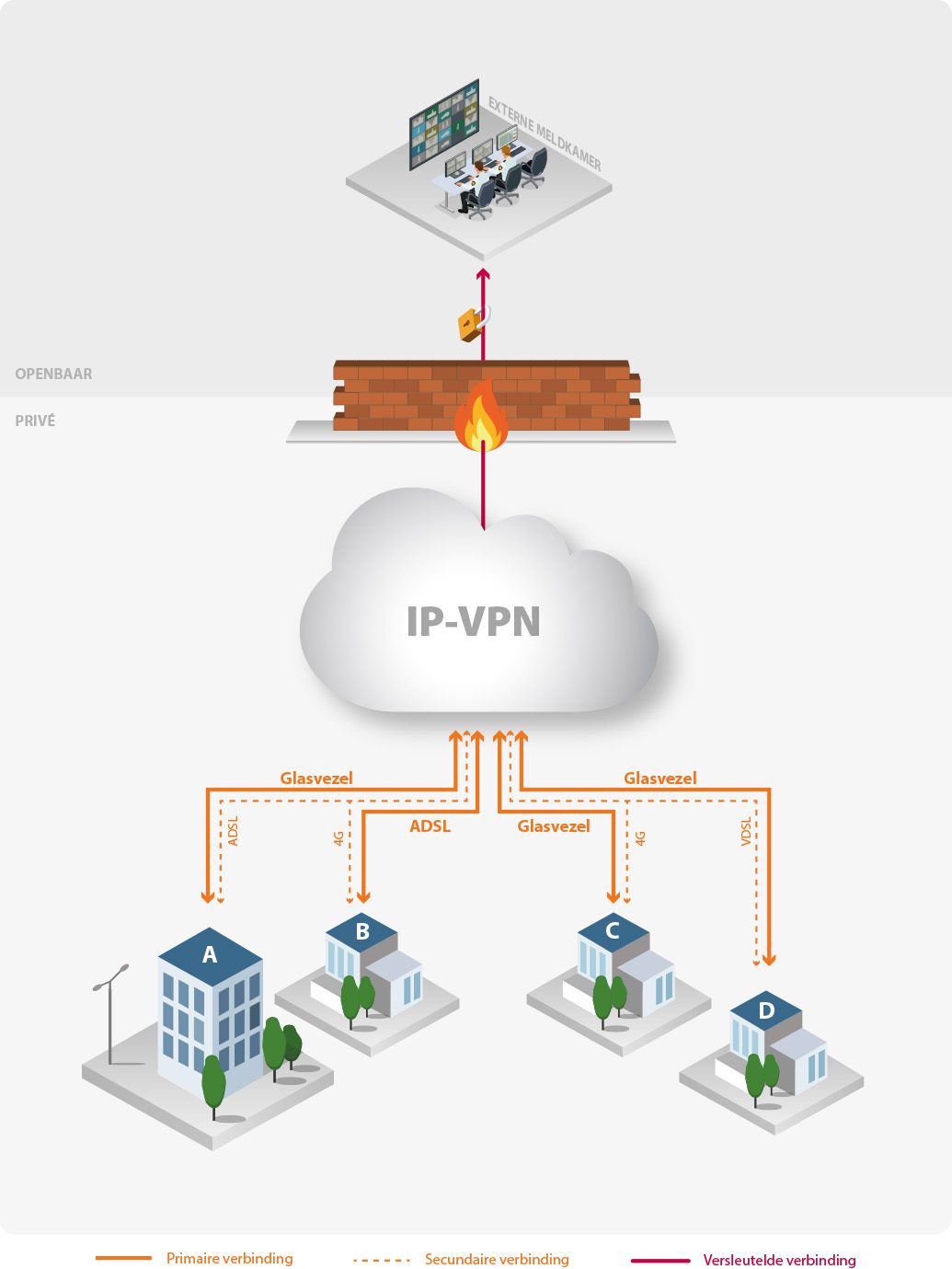
With an IP-VPN, data transport does not take place over the public internet but over a private IP network managed by a single network service provider. Multiple customers of this network service provider can use the same physical network, but the data streams of the various customers are strictly separated from one another. Each customer essentially has its own private network. Data can only be exchanged within this private network between the different locations of that customer. This happens outside the public internet; all connections go through the provider’s data center, and in principle, data cannot leave this network. This allows end-to-end guarantees for both the availability of the IP-VPN and the network performance.
Although the service provided is quite complex, as you can read, the configuration at the customer’s location is simple and affordable. Standard routers can be used within an IP-VPN.
There is one caveat we should mention. The transportation of data from the various locations to the data center is, in principle, unencrypted. This means that this data could theoretically be intercepted. If this poses too great a risk, Mactwin can implement encryption on these connections.
Medium and provider independent
With an IP-VPN, all (customer) locations are connected to the data center. The medium through which this connection runs (fiber optic, 4G, VDSL, ADSL, etc.) is irrelevant. If your telecom provider is not yet connected to the data center at a certain location, an (IP-SEC VPN) tunnel can be set up to connect that location to your IP-VPN. This makes the location part of your private network. The data traffic passing through this tunnel is encrypted, ensuring data integrity.
Redundancy
If redundancy is important for your organization, the IP-VPN solution can also be configured redundantly. A (passive) standby connection is set up, which is activated (manually or via an advanced router configuration) only when the primary connection fails. It is common to procure this standby connection from a different telecom provider, and ideally, it should run through a different medium. For instance, if the primary connection uses fiber optics, you might opt for a DSL standby connection. The standby connection does not need to be as fast as the primary one. The goal is to ensure that critical processes can continue if the primary line fails, even if there is a temporary delay.
External monitoring to an alarm receiving center
In some situations, a connection to the internet is still required. For example, to send alarm notifications to an external alarm receiving center. You likely do not want them to be part of your private network. Therefore, this internet connection is only possible via the data center and a highly secured internet connection. Only specific data, such as alarm notifications, can be sent to the relevant alarm receiving center. Decentralized locations are never directly connected to the internet. If you also want Mactwin to remotelymonitor and manage your security systems a similar connection to your IP-VPN can be established.
More information?
Mactwin has selected reliable network service providers to realize such connections. Do you want to connect multiple locations in a simple and cost-effective manner? Then contact one of our account managers for a custom solution.
