Detection principles at a glance
Detectors are deployed as part of a burglary protection system; a system that is aimed at identifying intruders as early as possible.
After all, the sooner an intruder is spotted, the more likely it is that they will be apprehended before they have reached their target.
Especially when delaying (structural) measures have also been taken.
Detection often starts with the outer shell, as soon as someone wants to enter the (company) premises.
Subsequently, detectors are placed in various places in the building itself.
The effectiveness of a burglar alarm system is determined, among other things, by the projection of the various system components and the coherence between the various electronic and structural measures.
Mactwin has developed OSVO® for this purpose.
OSVO is a model that can be used to design effective burglary protection.
The basic principles of OSVO are: signalling as quickly as possible, making structural delays within the detection field of the signalling and follow-up within the delay time.
It goes without saying that the delay time should be longer the farther away the nearest police post is.
How and with which (types of) detectors and delaying measures the burglar alarm system is built depends, among other things, on:
- Probability and expected impact of a criminal action
- the desired level of security
- The expected method of attack
- the desired delay time (depending on the follow-up time)
- On-site conditions and influences
In this article, we will limit ourselves to the different forms of detection.
Delaying (structural) measures are not taken into account, but they are indeed an essential part of an effective burglary protection system.
Below you will find an overview of the most commonly used and modern detectors.
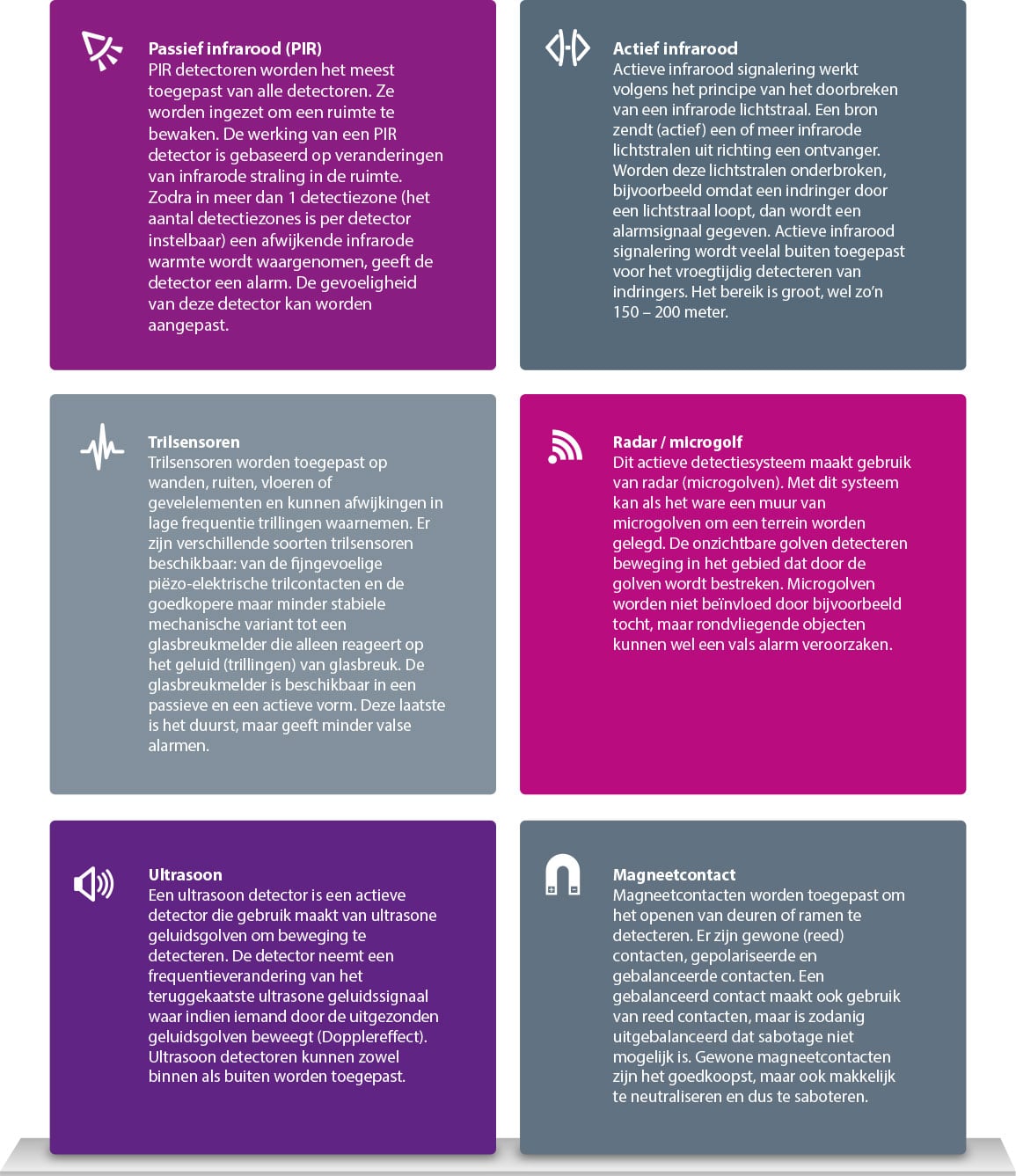

Manipulation possibilities
Some of the detection principles mentioned can be manipulated.
This is certainly not easy, but if the criminal has sufficient knowledge of the detectors and their operating principles, it is sometimes possible with some effort.
See also the infographic on the right.
The easiest to manipulate are the passive infrared detectors.
This is done, for example, by masking them, covering them or spraying them shut.
Fortunately, there are detectors with masking detection (anti-mask detection) on the market.
A good example is the PIR detector that continuously measures the light transmission of the screen.
Forwarding
The transmission of an alarm to a Private Alarm Centre is also an important part of a burglar alarm system.
This ensures that a burglar alarm is immediately followed up, usually after verification.
This significantly increases the criminal’s chance of being caught and may prevent theft of goods or business property.
Last autumn, the NEN amended a number of standards for alarm transmitters and receivers.
The NEN-EN 50136-2 specifies the technical requirements of alarm transmitters with regard to performance, reliability, safety and security characteristics.
The NEN-EN 50136-3 specifies the technical requirements of the alarm receiver.
Finally
If you want an effective burglary protection system, there are quite a few choices to make, such as the choice of detectors.
With this article, you will have a good handle.
However, keep in mind that an effective intrusion detection system consists of a balanced and coherent combination of signalling detectors (preferably different detection principles combined), structural delaying measures and a fast and safe notification to the Private Alarm Centre.

