Biometric Identification
Biometrics covers a variety of technologies in which unique identifiable characteristics of people are used for identification and authentication. These include (but are not limited to) a person’s fingerprint, iris print, hand, face, voice, gait or signature, which can be used to validate the identity of individuals.
These unique physical characteristics are difficult to forge. People always have these with them and they are also not transferable. In general, biometrics are a very reliable method of identification. By combining a card / tag with biometrics (two factor authentication), individuals may be identified very reliably.

Biometric Technology
Biometric systems can seem complicated, but they all use the same three steps. The first time you use a biometric system, it records basic information about you, like your name or an identification number. It then captures an image or recording of your specific trait. Then the system analyzes your trait and translate it into a code or graph. The next time you use the system, it compares the trait you present to the information on file. Then, it either accepts or rejects that you are who you claim to be.

Comparison Biometric Techniques
In the diagram below we have compared the most common biometric techniques. The diagram is part of the BIESS (Best Practice) implementation model for access control and helps you choosing the best technology in your situation.
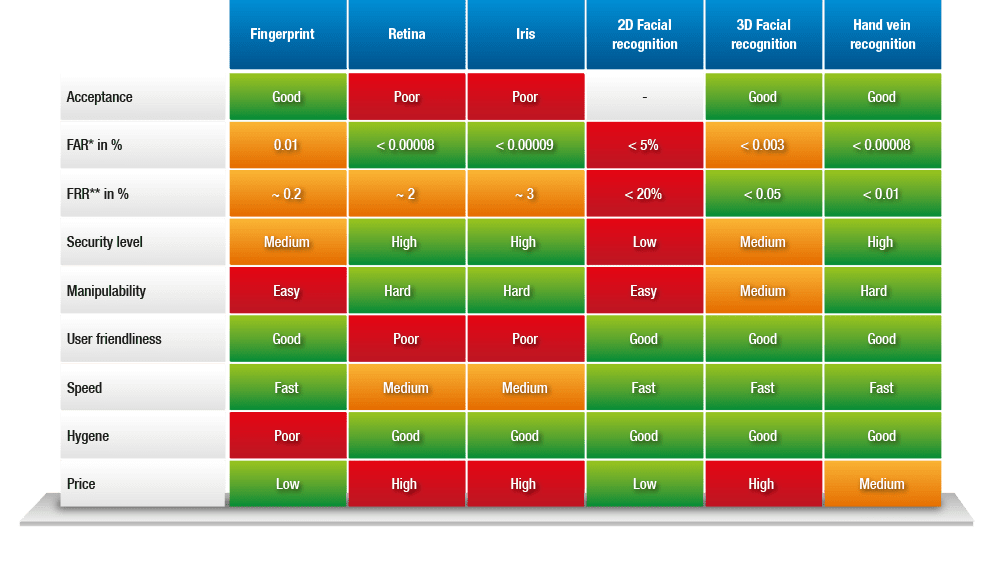
* False Acceptance Ratio
** False Rejection Ratio

Ask our Specialists
If you have any more questions about our security solutions, our specialists are ready to help you. They are happy to translate these solutions to your specific situation. Feel free to contact us!
Erik Poulussen
Account Manager
Call Erik direct: +31 (0) 26 479 22 08
